No, this post is not about schools or universities. This is about SSL/TLS security.
In order to secure an internet connection, SSL/TLS can be used. There are many ways to secure a network connection with SSL/TLS. You have ciphers and algorithms for connection setup and key exchange, ciphers for data stream encryption, hashing algorithms and most of those come in variants with different key lengths. So we talk about a Cipher Suites. A single cipher suite for example looks like this: “TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA_P256”.
Then there is history and backwards compatibility. Computers gets faster, resulting in secure encryption becoming insecure over time. So some encryption becomes obsolete but since functionality is more important than security, this obsolete encryption can still be used.
Different Windows releases come with different sets of cipher suites. For example, here is an overview of the TLS cipher suites in Windows 8.1 / Server 2012 R2. This Windows release supports insecure cipher suites such as SSL_CK_RC4_128_WITH_MD5. So this calls for action:
- Determine the enabled cipher suites.
- Decide which ones must be disabled.
- Disable the insecure cipher suites.
For determining the available cipher suites on your server, visit SSL Labs and scan your site. (which must be running https of course) Here you get your grade. Stop reading when it’s A or A+.
To decide which cipher suites must be disabled in order to improve your grade, you can use this Crypto IIS Tool which is windows only. This tool suggests the best set of cipher suites (step 2) and makes the required registry changes (step 3) if instructed to do so. Note that this tool also enables you to change the order in with the cipher suites are used when both sides try to agree on a cipher suite. This priority ordering is otherwise set with the group policy editor.
Now rate your site again and check your grade.
(Story based on this article: https://scotthelme.co.uk/getting-an-a-on-the-qualys-ssl-test-windows-edition/)
Attack Vector
The attack vector here is the fact that both sides negotiate and agree on a common cipher suite. A Man-in-the-Middle attacker will try to manipulate this negotiation and so try to force the use of an obsolete insecure cipher suite. Allowing only a single (the most secure one with 4096 bits asymmetrical keys, 512 bits encryption etc.) cipher suite will make your site immune to such an attack, but I guess that only the NSA will visit your site then…
Opera Security Badge
The green lock symbol next to https in your browser address bar does not indicate the use of a secure cipher suite. Even the obsolete and insecure ones (Single DES, MD5 hash etc.) might show up as green. The Opera browser shows this for my site
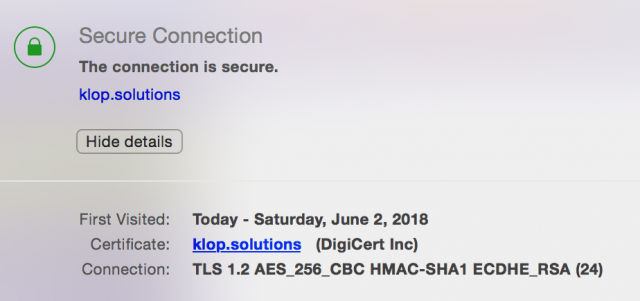
which gives a good summary of the connection security. Opera actually checks for outdated security (SSL v2, 40 or 56 bits encryption, RSA or DH key exchange with 900 bits or less) and will notify you (“The site is using an outdated encryption method”) and block the site. Info about this can be found here.